Basics of E-Discovery
Welcome to the second edition of Exterro's Basics of E-Discovery guide.
Few would argue the premise that successful companies depend on the creation and consumption of electronic data. But all that content and information introduces significant cost and risk into an organization. Because of the explosive growth in the amount of data that companies today create, collect, and store, they are spending millions of dollars in unnecessary storage and management costs, while also exposing themselves to the increasing risk of security, privacy, compliance and legal violations. It's against this backdrop that the concept of information governance (IG) has risen to prominence in recent years.
What is information governance?
You'll come across various definitions of information governance (IG), but a useful one comes from the analyst firm Gartner:
“The specification of decision rights and an accountability framework to ensure appropriate behavior in the valuation, creation, storage, use, archiving and deletion of information. It includes the processes, roles and policies, standards and metrics that ensure the effective and efficient use of information in enabling an organization to achieve its goals.”
- Gartner
We know there is a lot to digest in that definition. We'll try to break it into more edible portions. Here are some important points to know about IG:
1. Comprehensive Strategy
IG builds on the principles of traditional records management and enterprise content management. Those disciplines focus on the information lifecycle, how data is created, stored, organized, and ultimately deleted. IG encompasses a comprehensive strategy that helps organizations get the most value out of their digital information assets while minimizing potential risks. In that sense, IG is designed to guide records management and enterprise content management, not replace them, while also providing a framework for making smarter decisions with regards to what information is valuable and where it is best stored within the IT infrastructure.
2. Essential to Business Process
IG impacts many areas of the organization. Virtually every business process creates and relies on information to function effectively, so a company's IG strategy affects the entire organization, not just the IT and records departments.
3. Cross-Disciplinary
Creating an IG strategy is a cross-disciplinary activity that relies on a multitude of stakeholders across the organization including IT, compliance, records management, legal, security/privacy, and business unit leaders. The Information Governance Reference Model (IGRM) shown below provides a helpful graphical representation of the cross-functional nature of IG.
4. Relevancy
When properly implemented, an IG strategy will allow you to "separate the wheat from the chaff." That is, you will be able to focus on gaining insight and value from the content that actually has business value (estimated to be only about 30% of content in your network) while ignoring or deleting the redundant, obsolete, or trivial (ROT) data that is clogging your servers.
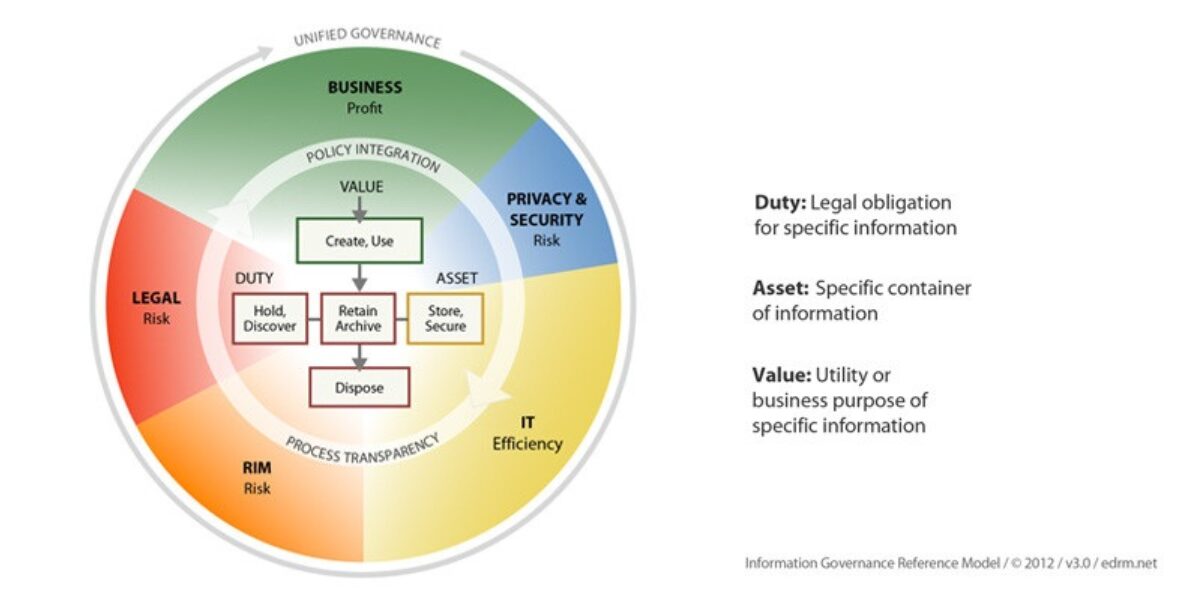
Information Governance Reference Model (IGRM)
Why Information Governance?
If you haven't noticed, we create a lot of data. The International Data Corporation (IDC) estimates that the digital universe doubles every couple years. Make no mistake, this explosion of data creates opportunities for companies. All this digital information, when properly harnessed, drives faster, smarter decision making, delivers better insights into consumer behavior, and promotes greater efficiency. But from a legal and risk standpoint, Big Data can also be difficult to manage. Studies vary by industry, but it's safe to say most companies never analyze the majority of the data they save. A recent Deloitte article estimates that 90% of data is unstructured, untagged, and untapped "dark data."
In the days before Big Data, decisions on how and where data should be kept were mainly made by the individual employees who created and used the data, and this is still a prevalent model. However, many companies have come to realize they need much more structure and centralized oversight into how data is stored, managed, and retained to protect against the inadvertent disclosure or hacking of sensitive information, such as personally identifiable information (PII), personal health information (PHI) payment card information (PCI), or other confidential data. Records management and content management programs are designed to perform this important function, but they tend to be applied reactively and have struggled to keep pace with the data deluge. And of course, there is always legal risk of information that could have been defensibly deleted hurting your case in future litigation if it is found to be responsive.
IG has emerged to fill this void by looking at information management much more comprehensively and proactively. If you revisit Gartner's definition above, you will see that IG is should connect the processes, roles, policies, standards, and metrics that traditionally have been managed as separate programs.
Though the price of data storage has fallen precipitously in recent years, that decline is far outpaced by the rate at which content is being created. Thus, data storage remains a significant cost drain for companies. That being said, a lot of people are hesitant to delete data, so IG can't be based solely on cost reduction. The more compelling reasons for adopting an IG program are the ability to gain greater insights from data that has business value and risk reduction. Significant data breaches can almost always be traced back to poor governance and create terrible publicity, damaging brands, and diminishing customer confidence. Examples from recent years abound, including Target, Equifax, Yahoo, Uber, and Sony.
Information governance unifies processes.
How does IG relate to E-Discovery?
You might be wondering why have IG in a guide about e-discovery. In fact, e-discovery and IG are very interrelated after all; IG is listed as the first stage of the Electronic Discovery Reference Model (EDRM).
Understanding the legal and regulatory obligations with which the enterprise must comply is essential to effective IG. To support e-discovery requests, IT managers and legal counsel must work together to deliver reliable and timely access to potentially relevant ESI. It is often difficult to meet court-mandated deadlines, because data is stored on numerous sources (e.g., file servers, content management systems, desktops, laptops, mobile devices, archives, and other storage assets), each with specific access requirements. Identifying which IT assets are most relevant to a case is the first step; systematically suspending disposition policies, preserving the ESI, and proactively de-duplicating, indexing, and searching the data is where the true importance of IG comes into focus. See our data mapping description below.
Other elements of IG that directly impact e-discovery activities include:
An effective IG strategy supports greater e-discovery efficiency by reducing the amount of discoverable ESI that is stored across the organization and improving how information is organized, so legal teams can get to what they need much quicker.
IG Challenges
Unlike the other sections of this guide that look at individual e-discovery processes, IG is a framework that isn't defined by specific stages or workflows. It serves to support and guide other processes and programs across the organization by establishing a common set of rules, policies, and procedures. This all begs the question: what does IG ultimately look like? There isn't an easy answer to that question. Many companies have started the IG conversation but have yet to move from theory to practice. And that jump isn't an easy one. Creating an IG program is full of many significant challenges. Here are three common hurdles.